Current News
/ArcaMax

Trump at hush money trial wishes Melania 'happy birthday' as testimony about trysts continues
NEW YORK — Donald Trump walked into his hush money trial Friday and wished his wife Melania a happy birthday — the day after former National Enquirer publisher David Pecker testified Trump never mentioned worrying about what she thought about his alleged affairs at the heart of the state’s case against him.
“I want to start by wishing ...Read more

R. Kelly's Chicago conviction to stand after high court rejects appeal
CHICAGO — R. Kelly’s sex-crime conviction and 20-year sentence in Chicago’s federal court will stand, an appeals court ruled Friday in a blistering opinion.
“For years, Robert Sylvester Kelly abused underage girls. By employing a complex scheme to keep victims quiet, he long evaded consequences. In recent years, though, those crimes ...Read more

California prison counselor sues CDCR, alleging discrimination and whisteblower retaliation
A corrections counselor at Pelican Bay State Prison in Crescent City is suing the California Department of Corrections and Rehabilitation for interest on back pay that was seized in what he described as whistleblower retaliation in response to him complaining of discrimination.
Joshua Kuzmicz has worked at Pelican Bay since March 2001, and for ...Read more
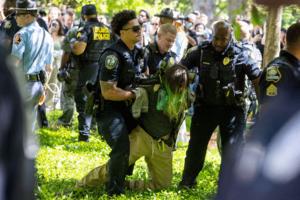
Emory president defends response to protests over Israel-Hamas war
ATLANTA — Emory University President Gregory L. Fenves said Friday he was “saddened” and “horrified” at protests that took place at the school Thursday, but said actions that disrupt the campus will not be tolerated.
The message to the school community came a day after at least 23 people were booked into the DeKalb County Jail on ...Read more

R. Kelly's Chicago conviction to stand after high court rejects appeal
CHICAGO — R. Kelly’s sex-crime conviction and 20-year sentence in Chicago’s federal court will stand, an appeals court ruled Friday in a blistering opinion.
“For years, Robert Sylvester Kelly abused underage girls. By employing a complex scheme to keep victims quiet, he long evaded consequences. In recent years, though, those crimes ...Read more

Trump at hush money trial wishes Melania 'happy birthday' as testimony about trysts continue
NEW YORK — Donald Trump walked into his hush money trial Friday and wished his wife Melania a happy birthday – the day after former National Enquirer publisher David Pecker testified Trump, after he announced his candidacy, never mentioned worrying about what she thought about his alleged affairs at the heart of the state’s case against ...Read more

No NYPD sweep overnight at Columbia pro-Gaza encampment, university president says
NEW YORK — The pro-Gaza encampment at Columbia University persisted Friday, after a deadline for students to clear the lawn of a series of colorful tents expired.
“There is a rumor that the NYPD has been invited to campus this evening,” university officials said overnight Thursday. “This rumor is false.”
“The talks have shown ...Read more

Opposing groups gather at Emory in Atlanta hours after protests lead to arrests
ATLANTA — Simultaneous gatherings were held at Emory University on Thursday evening, hours after an encampment on campus led to clashes with responding officers and multiple arrests.
A small group of Jewish students, local residents and officials stood outside Ali’s Cookies at Emory Village at 7 p.m. for a Passover gathering and to show ...Read more

Legislation to restructure United Methodists moves forward
United Methodist delegates have overwhelmingly endorsed a constitutional amendment many say could defuse debates over the role of LGBTQ people in the church. The amendment, approved Thursday at the denomination’s gathering in Charlotte, N.C., gives each region of the international church the ability to make their own decisions on divisive ...Read more

A judge has declared a mistrial in John Dougherty's extortion trial. What happens now?
PHILADELPHIA —Former labor leader John Dougherty's federal extortion trial ended in a mistrial Thursday after jurors declared they were at a stalemate and unable to reach a unanimous verdict, offering an inconclusive ending to the ex-union chief's third trial in as many years.
So, what happens now?
Why was a mistrial declared?
After 11 ...Read more
Trump wishes Melania “happy birthday” at hush money trial as testimony about trysts continue
NEW YORK — Donald Trump walked into his hush money trial Friday and wished his wife Melania a happy birthday – the day after former National Enquirer publisher David Pecker testified Trump, after he announced his candidacy, never mentioned worrying about what she thought about his alleged affairs at the heart of the state’s case against ...Read more

Nonfatal shootings in Kansas City have jumped 39% this year. Over 40 victims have been kids
Nonfatal shootings have spiked 39% so far this year, despite recent efforts at tackling Kansas City’s gun violence problem.
That uptick is in part attributed to the mass shooting at the Chiefs Super Bowl rally where two dozen people were shot and one bystander was killed on Valentine’s Day.
But even March saw a drastic increase — 42% —...Read more

NYPD hate crime cops investigating Israeli flag thefts as Gaza protests grip NYC
NEW YORK — The NYPD is investigating two recent Israeli flag thefts in Manhattan as hate crimes amid pro-Palestinian protests over the Gaza conflict continue to grip the city, officials said Friday.
In one of the two incidents, a Columbia University protester set the flag on fire after a rock was thrown at its owner, police said.
The first ...Read more

Georgia becomes focus of maternal health discussion with visit from Biden administration
ATLANTA — The Biden administration is confronting the country’s worsening maternal mortality rate with visits to multiple states, including Georgia on Monday, to focus attention on women’s access to health care.
The visit to Atlanta is part of a year-long initiative launched in January to expand the federal government’s work to address ...Read more
California's Riverside County deputy, 14 others arrested in drug trafficking bust
LOS ANGELES — Culminating a yearlong investigation dubbed "Hotline Bling," authorities in Riverside County have seized millions of dollars worth of illegal drugs and arrested 15 people suspected of helping a Sinaloa, Mexico, cartel's drug trafficking network, including a Riverside County Sheriff's deputy.
In collaboration with the Riverside ...Read more
Analysis: What to watch during what could be Biden's final White House correspondents' dinner
WASHINGTON — Joe Biden’s aviator sunglasses likely won’t be far away Saturday night when the president cracks some jokes at the annual White House Correspondents’ Association dinner. But not everyone will be laughing during Washington’s yearly spectacle — even if “Dark Brandon” makes another appearance.
That’s Biden’s ...Read more
California's Riverside County deputy, 14 others arrested in drug trafficking bust
LOS ANGELES — Culminating a yearlong investigation dubbed "Hotline Bling," authorities in Riverside County have seized millions of dollars worth of illegal drugs and arrested 15 people suspected of helping a Sinaloa, Mexico, cartel's drug trafficking network, including a Riverside County Sheriff's deputy.
In collaboration with the Riverside ...Read more
Ukraine detains First Minister in Zelenskyy's graft crackdown
Ukraine’s agriculture minister became the first cabinet member under Volodymyr Zelenskyy’s presidency to be detained in a crackdown on corruption demanded by allies as a condition for aid in Kyiv’s war against Russia.
The High Anti-Corruption Court in Kyiv ordered Mykola Solskyi, who has overseen Ukraine’s grain-export policy during the...Read more
Xi warns Blinken against 'vicious competition' between US, China
President Xi Jinping warned America’s top diplomat that the U.S. shouldn’t target or oppose China, as the world’s largest economies wrapped two days of talks spanning thorny disputes on trade and Beijing’s support for Russia’s war machine.
The Chinese leader met with U.S. Secretary of State Antony Blinken in Beijing on Friday ...Read more

Philadelphia has a lot more deadly shootings than expected for a big city − and NYC is much safer, new study says
Recent high-profile mass shootings at SEPTA bus stations have left Philadelphia commuters on high alert. Two gunmen opened fire at a bus stop in the Ogontz neighborhood on March 4, 2024, striking five people and killing 17-year-old Dayemen Taylor. Two days later, a group of teenagers shot eight other teens waiting at a bus stop near Northeast...Read more
Popular Stories
- Israel-Hamas war protesters clash with officers at Emory in Atlanta
- 'Bizarre': Why did Rand Paul miss the Ukraine foreign aid vote?
- Haiti enters new era of governing: Presidential council sworn in, prime minister resigns
- McAfee challenger out of contention for Fulton County judicial race, judge rules
- 2 arrests made, encampments taken down at Princeton following pro-Palestinian protests on college campus