Current News
/ArcaMax

OJ Simpson's cause of death confirmed
O.J. Simpson’s cause of death has officially been confirmed, just weeks after the former football star’s death at the age of 76.
Simpson — who had long been just as famous (if not more so) for his double-murder trial as his acclaimed athletic career — died of metastatic prostate cancer on April 10, his attorney and executor of his ...Read more

Kansas House votes to overturn Gov. Laura Kelly's tax cuts veto, with many Democrats joining Republicans
The Kansas House on Friday voted to override Democratic Gov. Laura Kelly’s veto of a sweeping tax package, which would eliminate one of the state’s income tax brackets, that she called too expensive.
Numerous Democrats joined Republicans to overturn the veto in a 104-15 vote. The override now heads to the Senate, where the legislation ...Read more

Tensions with insurers mount in Archdiocese of Baltimore bankruptcy case
BALTIMORE — Tensions are growing in the Archdiocese of Baltimore’s bankruptcy case around the role of the church’s insurers.
Baltimore’s arm of the Catholic Church, America’s oldest archdiocese, has sued its insurers for alleged breach of contract in one legal battle. In another argument, the insurers sought to block the committee of ...Read more

Trump at hush money trial wishes Melania 'happy birthday' as Pecker testimony about trysts continues
NEW YORK — Donald Trump wished his wife Melania a happy birthday walking into his hush money trial Friday — a day after former National Enquirer publisher David Pecker said the former president never mentioned worrying about what she thought about his alleged affairs at the heart of the state’s case against him.
“I want to start by ...Read more

King Charles to resume public duties next week, despite reports of funeral planning, says palace
King Charles has progressed enough in his cancer treatment that he’ll return to public duties next week for the first time since announcing his diagnosis, Buckingham Palace said Friday.
The news comes just one day after unnamed sources told The Daily Beast that the 75-year-old British monarch was “significantly more unwell than his aides ...Read more

White House drops plan to ban menthol cigarettes
WASHINGTON — The Biden administration on Friday announced it is dropping — for now ― a plan to ban menthol cigarettes after months of speculation about the proposal’s future.
Health and Human Services Secretary Xavier Becerra did not say when or if the administration would revisit the issue, nor did he mention the fate of a related ...Read more

Trump 'hush money' trial: Key takeaways from week one
The opening week of Donald Trump’s historic hush money trial offered plenty of insights into how his 2016 presidential campaign teamed up with a tabloid publisher to silence embarrassing stories from women who said they’d had extramarital affairs with him.
David Pecker, the former chief executive of the firm that published the National ...Read more

Athletic director at Maryland high school used AI to fake racist recording of principal, police say
BALTIMORE — Pikesville High School’s athletic director was arrested Thursday morning in connection with an artificial intelligence-made audio clip of the school’s principal having a fake, racist conversation.
Dazhon Darien, 31, is charged with disrupting school activities after Baltimore County Police say he created the falsified audio ...Read more

US Defense Chief confirms $6 billion arms commitment for Ukraine
WASHINGTON — Defense Secretary Lloyd Austin confirmed Friday a $6 billion commitment for long-term contracts to provide Ukraine with weapons such as Patriot missiles, artillery ammunition and drones.
Austin laid out a broad commitment but not signed contracts, which would be likely to take months to complete under the Ukraine Security ...Read more

Ex-American Airlines flight attendant accused of filming girl in Boston-bound plane's bathroom indicted
BOSTON — A former American Airlines flight attendant who’s accused of filming a girl in a plane’s bathroom on a Boston-bound flight has been indicted, according to the feds.
Estes Carter Thompson III, 36, of Charlotte, North Carolina, also allegedly had recordings of four other girl passengers using airplane lavatories.
Thompson was ...Read more
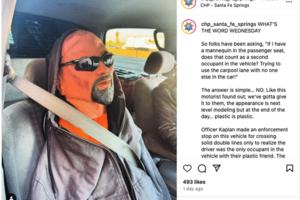
Carpool lane driver in LA caught with mannequin in the passenger seat
LOS ANGELES — Los Angeles traffic is so notoriously bad, some residents might be willing to do anything to cut down on wait time — including driving with a mannequin in the passenger seat.
A California Highway Patrol officer in Santa Fe Springs stopped a driver recently for crossing solid double lines to enter a carpool lane, only to bust ...Read more

Kim Kardashian meets with VP Harris, pardoned prisoners at White House
Kim Kardashian made a return to the White House this week to discuss criminal justice reform with Vice President Kamala Harris.
The reality TV star — and billionaire business mogul — joined a roundtable discussion Thursday regarding the 11 pardons issued and five sentences commuted by President Joe Biden the day prior.
Kardashian was ...Read more

KC police officer who ran anti-crime charity indicted for wire fraud, money laundering
KANSAS CITY, Mo. — A Kansas City police officer has been indicted on 14 federal counts of wire fraud and two counts of money laundering, the U.S. Attorney’s Office for the Western District of Missouri announced Friday.
Aaron Wayne McKie, 46, has been a Kansas City Police Department officer since April 2000.
The charges allege he took ...Read more

Buckingham Palace, UK government reviewing 'unwell' King Charles' funeral plans, report says
Buckingham Palace and the British government began reviewing hundreds of documents related to King Charles III’s future funeral following the monarch’s cancer diagnosis, according to a report.
Little is known about Charles’ mysterious illness outside of his initial announcement of “a form of cancer” in February, but sources close to ...Read more

Baltimore businesses sue Dali owners for negligence in Key Bridge collapse
BALTIMORE — A Baltimore publisher is suing the companies behind the massive cargo ship that collapsed the Francis Scott Key Bridge last month, saying they were negligent for allowing an allegedly unseaworthy ship to sail ahead of the catastrophic crash that killed six people.
American Publishing LLC, based in Essex, filed the proposed class ...Read more

Why Arnold Schwarzenegger's 2003 tabloid deal came up at Trump's hush money trial
Former California Gov. Arnold Schwarzenegger’s past personal foibles reemerged in the trial of former President Donald Trump over allegations of a hush money payment to a porn star in an attempt to cover up their sexual relationship.
Former National Enquirer Publisher David Pecker testified this week that he was reluctant to pay off a Playboy...Read more

Judge refuses to let accused ISIS supporter take wedding trip to West Bank amid concerns
DETROIT — A federal judge Friday refused to let an accused Islamic State supporter convicted after an FBI counterterrorism investigation travel to the West Bank this weekend to attend a wedding while under court supervision and amid the Israel-Hamas war.
U.S. District Judge Terrence Berg concluded letting Ypsilanti resident Yousef Ramadan, 35...Read more

You're gonna need a bigger number: Scientists consider a Category 6 for mega-hurricane era
In 1973, the National Hurricane Center introduced the Saffir-Simpson scale, a five-category rating system that classified hurricanes by wind intensity.
At the bottom of the scale was Category 1, for storms with sustained winds of 74 to 95 mph. At the top was Category 5, for disasters with winds of 157 mph or more.
In the half-century since the...Read more

Pummeled by airstrikes, Ukrainians in Kharkiv defy Russia by getting on with daily life
KHARKIV, Ukraine — It made for an unlovely municipal symbol, soaring but hardly graceful: the 800-foot-tall Soviet-era television tower that was for decades a familiar signature in the skyline of Ukraine's second-largest city, Kharkiv.
Ungainly though the tower may have been, the sight of its red-and-white upper mast plunging spearlike to ...Read more

In interview with Howard Stern, Biden says he considered suicide after death of first wife and daughter
NEW YORK — President Biden Friday said he considered killing himself after his first wife and baby daughter died in a car crash shortly after he won election as a U.S. senator.
In an interview with radio host Howard Stern, Biden admitted being distraught after his first wife, Neilia, and 18-month-old daughter, Naomi, died in a 1972 crash.
�...Read more
Popular Stories
- Haiti enters new era of governing: Presidential council sworn in, prime minister resigns
- Pro-Palestinian protests grow at UCLA and UC Santa Barbara
- Harvey Weinstein rape conviction overturned by NY appeals court; California conviction remains
- At UC Irvine, hundreds turn out to demonstrate in support of Palestine
- Nevada boy with autism found in metal cage, parents arrested





